sqlmap-gui
GUI for SQLMAP, a powerful tool for automated SQL injection
sqlmap-gui
sqlmap-gui is a Python-based graphical user interface (GUI) for interacting with the powerful sqlmap penetration testing tool. This GUI simplifies the use of sqlmap, enabling users to execute SQL injection tests and analyze vulnerabilities without requiring extensive command-line experience.
Features
- User-Friendly Interface: Simplified navigation for sqlmap functionalities.
- Comprehensive Options: Access to all popular sqlmap commands with categorized tabs.
- Results Display: Real-time output display for executed sqlmap commands.
- Cross-Platform: Runs on Windows and
Linux(working). - Customizable: Easily add new features or extend the interface.
Screenshots
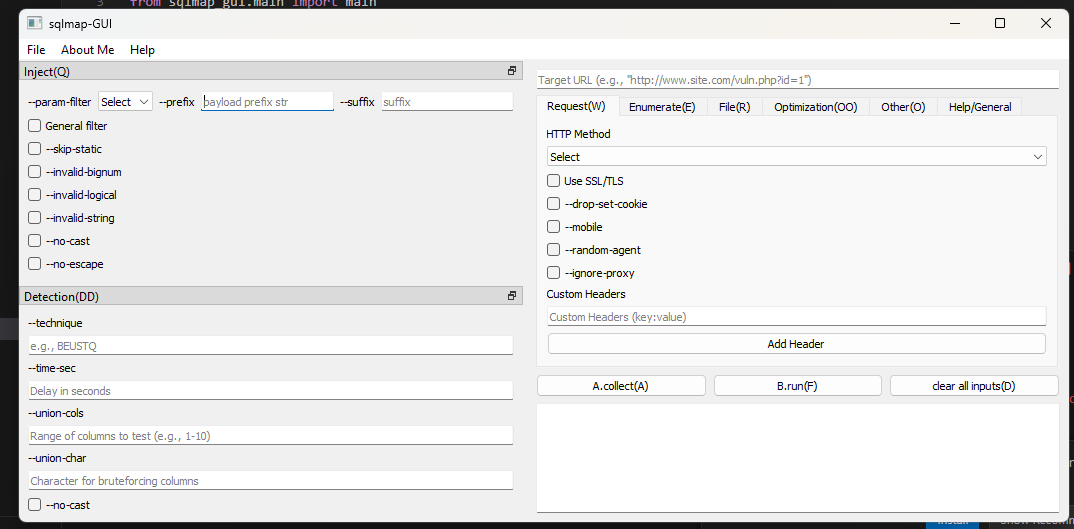
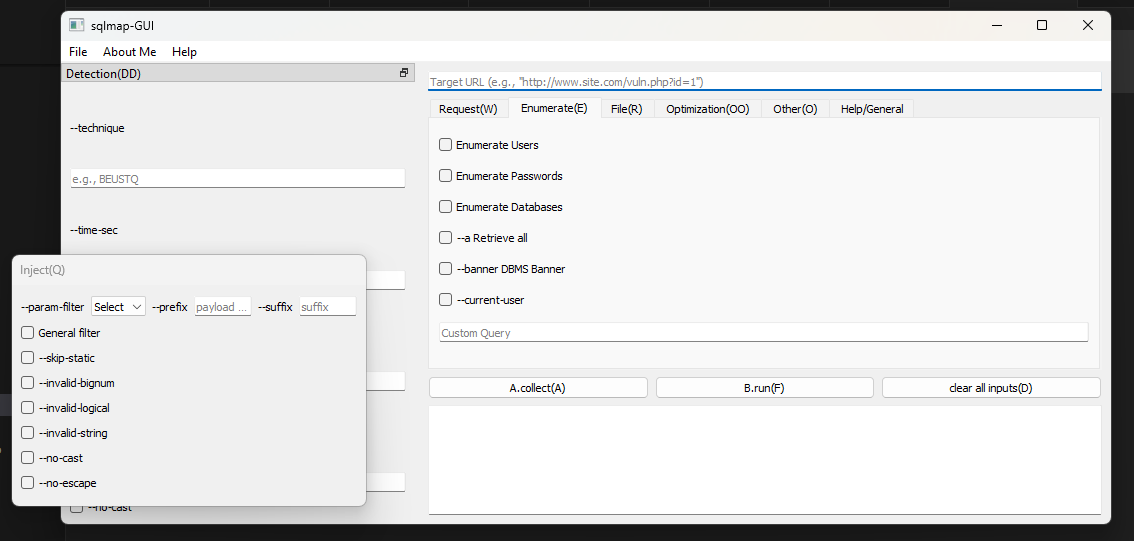
Installation
Follow these steps to set up the project locally:
Clone the Repository
git clone https://github.com/raselmandol/sqlmap-gui.git
cd sqlmap-gui
Create a Virtual Environment
python -m venv sqlmap_env
sqlmap_env\Scripts\activate # Windows
Install Dependencies
pip install -r requirements.txt
Build
pip install -e .
Run the Application
python sqlmap_gui
Build Executable (Windows)
if you want to build an .exe:
Install PyInstaller:
pip install pyinstaller
Note: Already added in
requirements.txt. (If you want to ignore it, make sure to remove it fromrequirements.txt.)
Convert your PNG icon to ICO.
Run:
pyinstaller --name sqlmap-gui --onefile --windowed --icon=icon.ico sqlmap_gui/main.py
Builder Script (builder.bat)
Usage
Run the script with one of the following flags:
builder.bat --build
Builds the project using pip install -e .
builder.bat --run
Runs the main application using python sqlmap_gui.
builder.bat --exe
Builds a standalone executable using PyInstaller. Configuration parameters are loaded from config.txt.
Note: To use
--activate, run./builder.ps1 --activateinstead of./builder.bat --activate. The PowerShell script (builder.ps1) is more reliable and effective in PowerShell environments, which are commonly used as the default terminal in most IDEs (such as Visual Studio Code).
How to Use
- Launch the GUI (
python sqlmap_gui). - Navigate through the tabs to explore sqlmap commands:
- Injection Tests: Enter a target URL and customize sqlmap options.
- Advanced Options: Configure sqlmap payloads and settings.
- Execute the command and view results in the output console.
Example
Here is a sample workflow for detecting vulnerabilities on a target website:
- Enter the target URL:
http://example.com/page?id=1. - Select detection options like:
- Technique:
--technique=T - DBMS:
--dbms=mysql
- Technique:
- Click
Runto execute sqlmap. - View results in the output console.
More
To get a list of basic options and switches use:
-h
To get a list of all options and switches use:
-hh
To get an overview of sqlmap capabilities, a list of supported features, and a description of all options and switches, along with examples, you are advised to consult the user’s manual. Use extra/optional command input option to use those extra options and switches. You can find Custom Query option in Enumerate tab.
Requirements
- Python 3.8+
- PyQt5
- sqlmap source
Contribution
Contributions are welcome! To contribute:
- Fork this repository.
-
Create a new branch:
git checkout -b feature-name -
Commit your changes:
git commit -m "Add new feature" -
Push to your branch:
git push origin feature-name - Open a pull request.
License
This project is licensed under the MIT License, sqlmap license.
To-Do
- Enhance error handling.
- Builder.bat script
- Option to load Sqlmap source/folder selection
- Improve documentation with more examples.
- More tabs/ more options
- JSON import, export
- History Tab
- Optimization tab
- Burp proxy
- sqlmap web
- Clean terminal/editor
- GitHub pages with documentation


